What is the PI network?
Despite the years of delay, mysterious operations and doubt on a large scale, the PI network still takes a semi -worship -like follower.
Critics, however, called the project.the money“Noting its dependence on ads within the application, the growth moved by the referral and central control in the symbols. Some even claim that the customer’s requirements (KYC) can allow user data customization.
The question is simple: How does the cryptocurrency that it claims to operate with mobile phones, which are criticized due to bottlenecks and limited interest, keeps millions of people honestly clicking on a button every day?
Launch in 2019 by Stanford founders, PI network I began to re -imagine encryption mining. Instead of the intensive energy devices, “Mine” PI (Bay) Metal currencies through the smartphone application.
The project depends on SEO (SCP) Protocol (SCP) And social “security departments” instead of proving work (POW), which promises a wider insertion of retailers.
In February 2025, PI finally to open Mainnet, which is long -awaited for foreign trade and distinguished symbol, after years of the original promise.
But the exhibition stumbles. Delaying immigration, kyc accumulation and unequal access Leave a lot of frustration. Nevertheless, a strong Hype withstood: Pay a short career Pi price about $ 3 before sliding to about $ 0.34 by September 2025.
To date, Pi Network continues to maintain great enthusiasm while facing operational and structural interests.
Do you know? The first “laptop” madness was not PI. in 2017,, A project promise called Electroneum, to mining smartphones, but it faded after the exchanges were lost.
Criticism and red flags
While the PI network continues to attract a large size of daily users, critics argue that its organization is full of flaws that have not been resolved.
Central and control of the basic team
Although PI holds itself a “open network”, control is still concentrated in the hands of its primary team. everyone Script It remains run by the project developers, no By members of independent society. This undermines decentralization that has been built most cryptocurrencies.
Excavator symbol and distribution
PI sets a maximum of 100 billion symbols, Divided Between four buckets: 65 % for community mining rewards, 20 % for the basic team, 10 % for basic reserves and 5 % for liquidity. On paper, this is evident, but the actual circulating numbers depend on the number of coins that moved to Mainnet. Each category opens only in a step with the verified migratory mining bonuses (MMR).
Referral -based rewards with aspects of young men
PI mining depends Hardly On referrals and “security departments”. Critics Argue This recruitment system reflects multi -level marketing plans, which now raises sustainability questions after the new user growth slows down.
Limited lists and liquidity issues
Even after February 2025 Mainnet launchPI trading places are still limited to medium -level exchanges such as OKX, Gate.IO, Bitget and Mexc. The main platforms such as Binance and Coinbase blocked the menus, noting that they were not resolved about the distinctive and central symbol.
Disclical volatility and symbolic activity
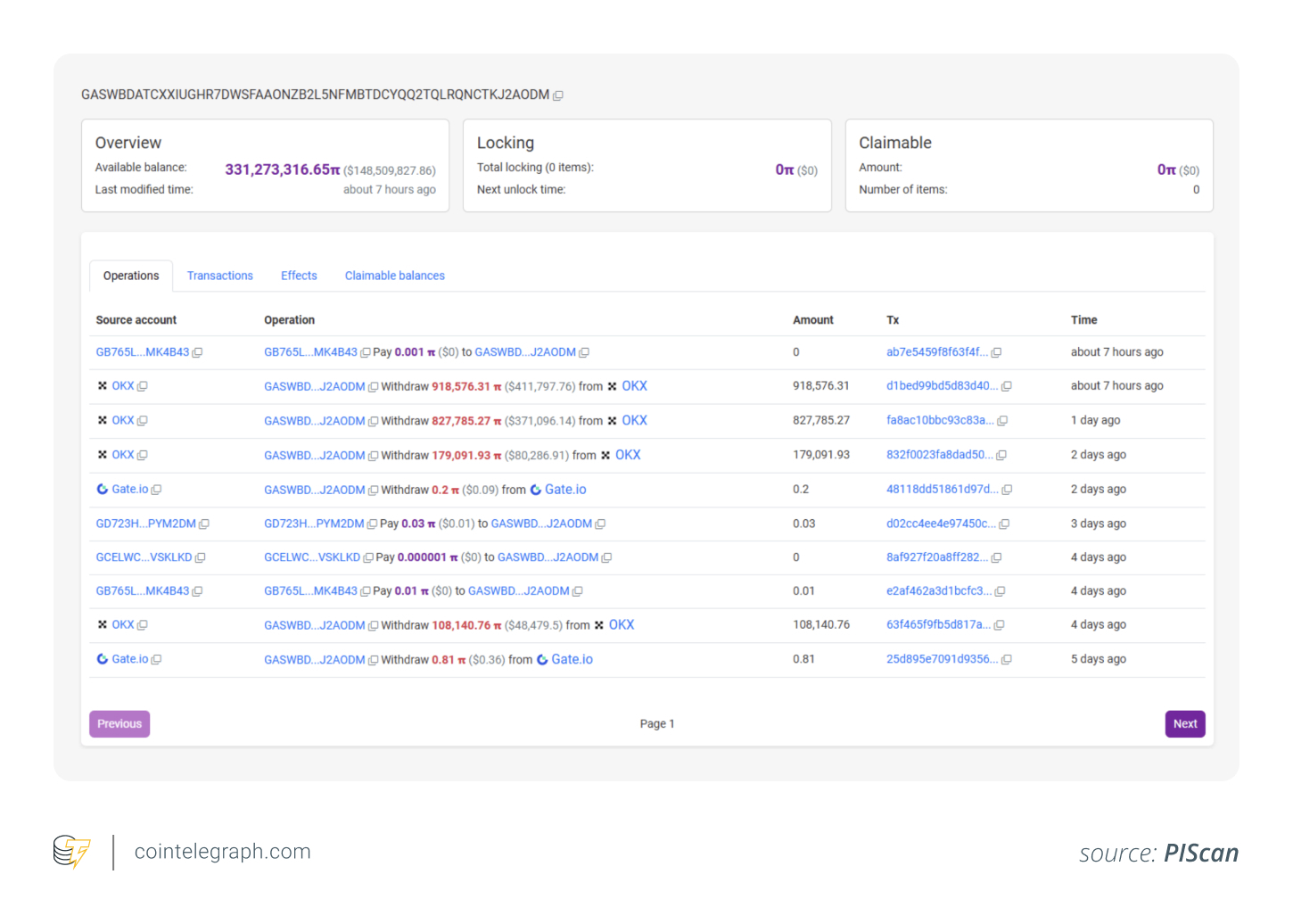
The PI’s market performance has been weak: since early 2025, it is close to $ 3 to about $ 0.34 -0.35 dollars as of September 3, 2025 (90 % disruption). Meanwhile, a coding portfolio bearing the name “Gas … ODM” quietly 331 million PI coins collectedMore feeding doubts about the attached activity from the inside.
Central Kyc Privacy Risks
To transfer the Biped Pi to Mainnet, users must first pass Learn about your customer (kyc). This means downloading an ID issued by the government and completing the “Selfie Live Selfie” check. Reports Indicate This data is stored on central servers instead of the user -controlled systems, which led to criticism about the risks of privacy and security.
Fears are not new: Previous allegations Issues with KYC service providers from a third party Constant questions have been fueled about how PI deal with sensitive user information and whether there are sufficient guarantees.
Do you know? Modern Internet Analysis The best visitors to Minepi.com by country: Vietnam (10.2 %), South Korea (8.2 %), India (6.66 %), the United States (6.6 %) and Ethiopia (5.2 %).
Why does the noise continue
Free mining, social reinforcement, and fixed ecosystem signals to preserve emotionally invested millions (even with a focus on gaps in liquidity and limited and central lists).
Low entry barrier, minimal financial risk
Mining PI cost attention instead of capital. Users simply open the application once for each session to confirm the activity (without graphics processing units, not electricity bills).
This frame reduces the perceived risk and makes the network within the reach of anyone who has a smartphone. Incentives with layers, such as referral reinforcements (25 % per active invitation) and security circuits (up to 100 % bonus), the experiment is manifested, and the informal benefit turns into gradual progress.
The access and first design of the mobile phone
PI markets itself as “encryption for the era of smartphone.” Instead of the governor and Mining platformsParticipation is reduced to one routine. Analysts highlight this as the real innovation of PI: it transforms non -technical users or who suffer from bank deficiency or encouraging into participants through a lightweight and effective system (SCP instead of POW).
Community identity as momentum
Important designations. PI users themselves call themselves “pioneers”, rituals such as daily taps, referrals and team building create social glue.
Campaign such as pifest And “PI Map” enhances activity, giving participants a sense of belonging. Even if the number of “60 meters users” for PI is discussed, the activity that has been verified around 12 million Accounts are still huge according to encryption standards.
Experience and hope for immediate benefit
I intentionally list the long -term project: Create a user fee first, then expand the utility. This sequence allows the reshaping of setbacks such as delaying deportation or reformulating delicate lists as temporary obstacles. For believers, the vision is more important than the present.
Continuous development signals
The momentum is also alive by the ecological system signals: HackathonsGrant the developer and construction boxes. These are not final products, but they give societal monuments to track and talk about, and help maintain participation between market fluctuations.
Do you know? more than 6.9 billion Smartphones are being used all over the world in 2025, which means that the first mobile encryption experiments such as PI may have a larger market of processing from Bitcoin portfolios, which number about 460 million.
What do you see next?
The power of staying in PI was not around a short -term price. The real test is whether it can turn the curiosity of the mass into an open network tool.
For observers, the signals to see are clear:
- Decentralization in practice: Evidence that the “open network” means more than a logo. Independent auditors and real integration (not only the messages inside the application) are the key.
- Lists and liquidity: Even exchange Like Binance steps, the price discovery and user confidence will remain limited.
- Ecological system delivery: Hackathons funded, live applications and active use is much more issue than blog updates.
- KYC and Immigration Progress: Olchain users will form the base of any functional economy.
If these landmarks advance forward, the PI noise may start to turn into a test. If they stop, faith (not the basics) remains the main product of the project.




