Bitcoin quantum: harvest now, decipher it later
Quantitative computers can quietly break Bitcoin, and one of the former infiltrators says that the countdown has already begun.
David Carvalho, a teenage teenage teen You may not stand up to the wave coming from quantum computing And AI -Breakthsists.
In the midst of his warning, there is a tactic known as “harvest now, deciphering later”, where the attackers distort the inventory Bitcoin encrypted transactions Today, waiting for future machines is strong enough to break the special keys.
Carvalho’s story adds weight to his warnings. The penetration began at the age of thirteen, as he later presented the advice of NATO and Fortune 500 companies before the establishment of the Naoris Protocol. Now this alarm emerges Bitcoin gaps in quantum computing Real can face the protection of the SHA digital signature algorithm and the elliptical curve (ECDSA) is a silent collapse of bitcoin systems if the industry is frequented in promotions.
Do you know? Google’s quantum chip showed an amazing standard for speed, solving problems in minutes that will take the fastest classic computers about 10 x 10 years.
Weakness in Bitcoin for quantum computing
Bitcoin depends on the Shamcin Check: SHA -256, which protects the mining process and the integrity of transactions, and ECDSA, which secure special keys behind the signatures that today’s machines consider unbridled.
Under the classic account, Imposition None of the system will take longer than the age of the universe, but the quantitative threat of Bitcoin changes this equation.
Blograms like Shore One day can allow a powerful quantum computer to extract a special key from a Public key In minutes, which makes it possible to kidnap the money from any exposed address before the transaction settles.
Security experts stress that the security currency security does not mean “even safe Q – Day“State actors and electronic crime groups are already working to harvest data for harvest now, as they decipher the subsequent encryption risk, and build archives quietly, hope to cancel it when you catch the devices.
mix Artificial intelligence in encryption Quantum technology may speed up this schedule significantly. Carvalho argues that artificial intelligence can help determine the weaknesses of Blockchain, while Quantum Hardware provides raw energy to exploit it. This combination – “How can break AI and Quantum Bitcoin”, as it offers – can progress on the day when the current encryption is no longer.
Exposure is already measurable. Almost 25 % -30 % of all bitcoin -about 6 million to 7 million bitcoin (BTC-Sitting in the types of old addresses such as paid to the public key (P2PK) or the retrora of P2PK. These formats reveal public keys, which makes them weak immediately once the quantum attacks become possible. Those Asleep The reused coins are a large part of the circulating BTC, thus stabilizing bitcoin prices in general and confidently dependent on bitcoin.
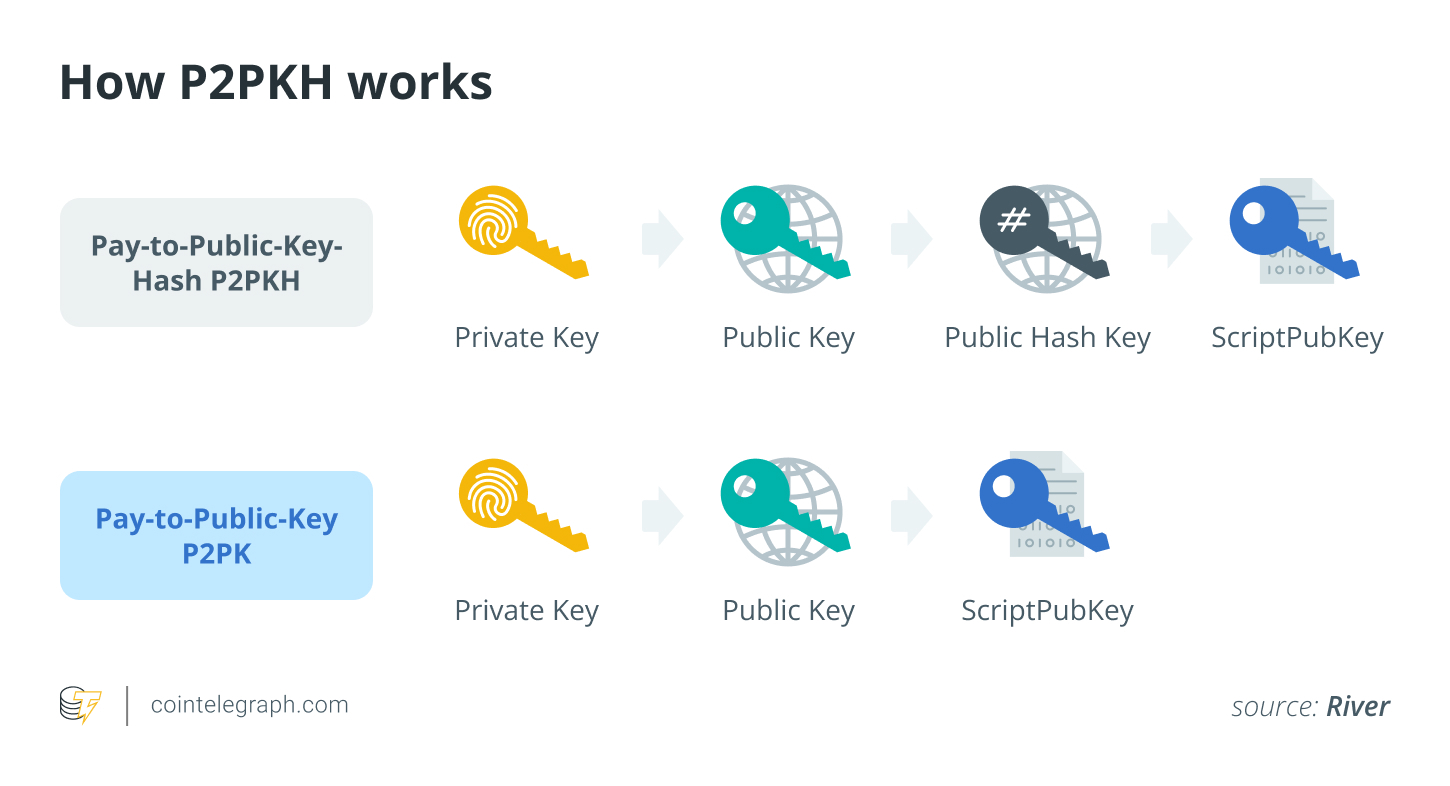
Meanwhile, agencies such as the National Institute for Standards and Technology and the National Security Agency are already urging a focus of post-quarter encryption in encryption, while setting immigration targets in 2030-2035 to protect critical systems. If Bitcoin’s upgrade is delayed, a global case study in Bitcoin may become QUANTUM – a conflict between the world’s leading digital assets and a new category of computing that rewrites the rules of protecting digital assets and Cleated currency security.
Carvalho warns the transitional window already narrow. Without updating the decisive bitcoin encryption and investment in the security of the quantitative Blockchain, it is afraid that the industry will discover it too late that the risk of quantum disorder was not “one day”.
Do you know? Device studies indicate that breaking the ECDSA key with the Bitcoin Wortico is within one hour (optimistic) requires about 13 million logical nets (or more than 300 million physical youth, depending on error correction systems).
Silent collapse of bitcoin systems?
David Carvalho warns what he calls a “silent collapse of Bitcoin systems”, a new strain of quantum attacks that depend on artificial intelligence that can break signatures, transfer boxes and detect the entire circumambulation.
Instead of exploiting the main title, these attacks will slowly establish confidence in Blockchain itself, and reshape the balances and consensus without leaving clear criminal traces.
In this vision, traditional security measures will be proven almost useful. Hurricane testsYou may miss the anomalies – detection and even the International Energy Agency contract to miss all the breach. Amnesty International can automatically investigate the weak spots in Blockchain encryption, simulating network behavior and adapting its tactics during flying, while Quantum machines Quietly, a special key crisis in the background.
Carvalho’s explicit warning: There will be no group of algorithm over the work. Instead, integrity will be invisible – the missing people here, the governance was quietly voted there, and money is incomprehensible – until Bitcoin’s adoption suffers from a crisis of confidence.
Explanation of Blockchain security resistant to quantity
The developers take the quantum threat of Bitcoin seriously, and many defensive efforts are already in implementation. However, they reveal how difficult it is true.
- BIP – 360 (Payment – Resistant – Resistant – Resistant, or P2QRH) Provides the quantitative resistance and hybrid addresses. This allows Bitcoin to gradually deport to post -code in encryption systems, which leads to a new protection situation without breaking old cases overnight.
- Like postutum post -infrastructure companies Nawras Protocol It builds decentralized networks designed to include Blockchain resistant to the quantitative resistant in the transactions layers, with the discovery of a real time threat with encryption that does not depend on weak elliptical curves.
- Safe quantum techniques such as Zero -based zero knowledge They gain an interest in retail proof systems, which avoid many weaknesses that are expected to be exploited.
But even the best solutions face a reality examination: Bitcoin’s Power is decentralizationThis makes difficult sweeping ups in. Bitcoin’s encryption update (especially depths such as replacing the basic signature plan) requires a wide agreement between miners, knots operators, service providers and users.
Even after consensus, the migration itself will be slow and anarchism. Millions of users will need to transport metal currencies from Legacy addresses to quantitative addresses. If the kiosks are adopted, the old currencies will remain exposed, which undermines the goal of the coded currency security in the encryption security in the quantum era.
Do you know? The Naoris Sub-Zero Layer can stick to the default Blockchains compatible with the device within 48 hours, providing post-raid protection without operating solid chocolate or disabled current contracts.
Crypting security in the era of quantum
Not everyone shares Carvalho.
Michael Sailor, CEO of the strategy, has Bitcoin, against the quantitative narration, refused to be exaggerated. Speaking on CNBC, it is framed It is “a way to circumvent the quantum marketing,” noting that companies like Google or Microsoft will not issue machines capable of breaking their encryption and that “Bitcoin can be promoted.”
The feelings of the wider experts are less refusal, but are still measured. Many horizon encoders see the risks of the weakness points in Bitcoin for quantum computing that extends for one or more nodes, indicating the most cautious estimates to 2040s. Optimists say that the turning point may not reach until 2035; Faming people warn that it may come within five to 10 years.
Panic is not fruitful, but contentment may be worse. Most of the professionals of cryptocurrencies are now agreed to prepare for how to penetrate quantum computing Bitcoin Governor Safety more escape later.
If Bitcoin defenders coordinate the protection of digital assets today, the transition to post -Quantum in Crypto may seem like a controlled upgrade. Delay for a long time, and can look more like “silent collapse” than Carvalho’s concerns.