Key takeaways
-
Buterin believes there is a 20% chance that quantum computers will be able to break current encryption before 2030, and he believes Ethereum should start preparing for this possibility.
-
The main risk involves ECDSA. Once the public key appears on the chain, a future quantum computer could, in theory, use it to retrieve the corresponding private key.
-
Buterin’s quantum emergency plan includes rolling back blocks, freezing EOs, and moving funds to quantum-resistant smart contract wallets.
-
Mitigation means smart contract wallets, NIST-certified post-quantum signatures, and flexible cryptographic infrastructure that can swap schemas without chaos.
In late 2025, Ethereum co-founder Vitalik Buterin I did something extraordinary. He puts numbers on risks that are usually discussed in science fiction terms.
Citing forecasting platform Metaculus, Buterin He said There is “about a 20% chance” that they are quantum computers Able to break encryption today It could arrive before 2030, with average projections approaching 2040.
After a few months at Devconnect in Buenos Aires, he… to caution This elliptical-curve crypto, the backbone of Ethereum and Bitcoin, “may break before the next US presidential election in 2028.” He also urged Ethereum to move to quantum-resistant foundations within about four years.
According to him, there is an unparalleled chance that a quantum computer related to cryptography will arrive in the 2020s; If so, the risk is on the Ethereum research roadmap. It should not be treated as something for the bucket in the distant future.
Did you know? As of 2025, Etherscan data He appears More than 350 million unique Ethereum addresses, highlighting the reach of the network even though only a small share of those addresses hold meaningful balances or remain active.
Why quantum computing is a problem for Ethereum crypto
Most of Ethereum’s security is based on the Elliptic Curve Discrete Logarithm (ECDLP) equation, which is the basis of the Elliptic Curve Digital Signature Algorithm (ECDSA). Ethereum is used secp256k1 Elliptic curve For these signatures simply:
-
for you Private key It is a large random number.
-
Your public key is a point on the curve derived from this private key.
-
Your address is a hash of this public key.
In classical hardware, going from a private key to a public key is easy, but going back is thought to be computationally infeasible. This asymmetry is why a 256-bit key is treated as effectively unguessable.
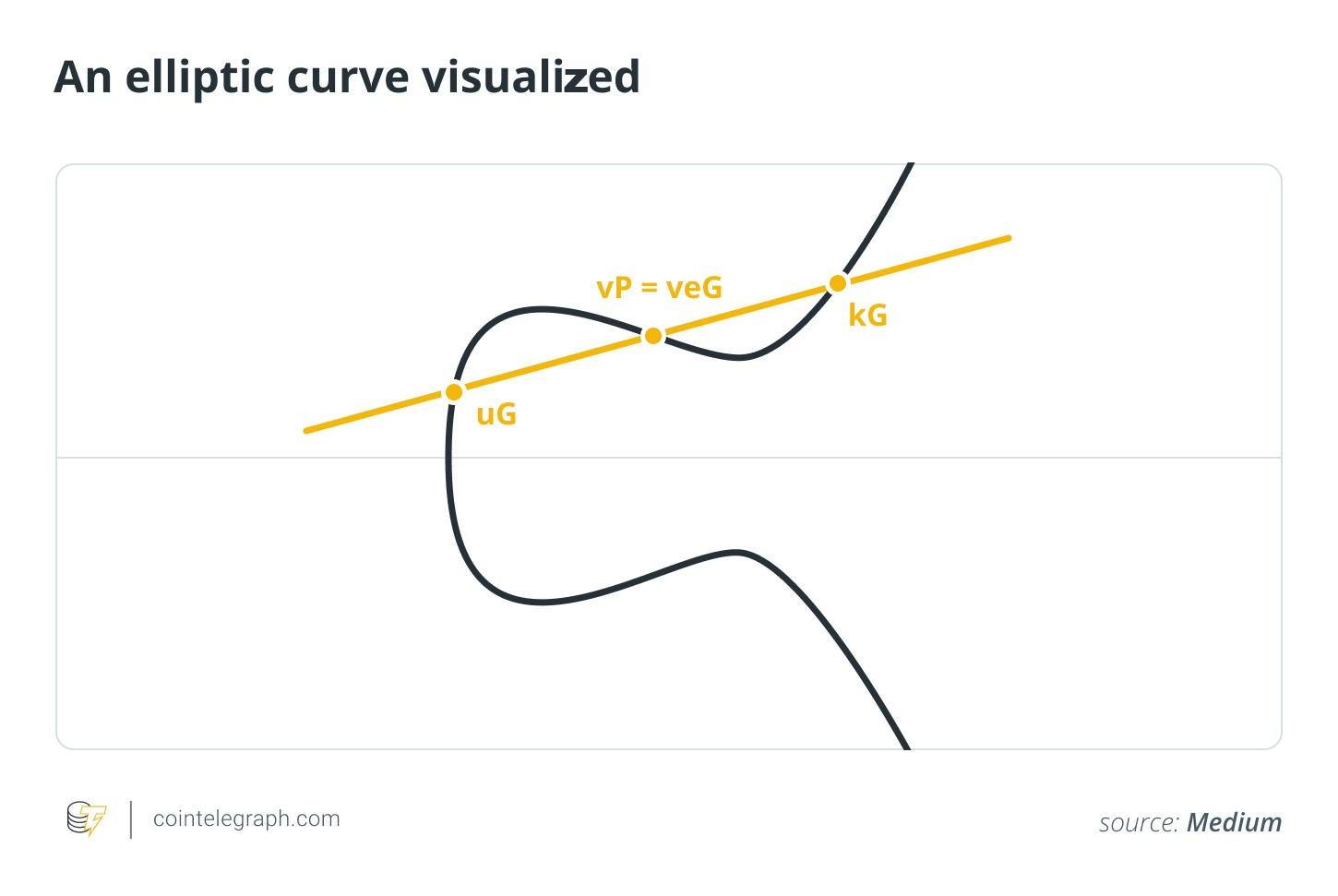
Quantum computing threatens this asymmetry. Shor’s algorithmproposed in 1994, shows that a sufficiently powerful quantum computer could solve the discrete logarithm equation and related factorization equations in polynomial time, which would undermine schemes such as Rivest-Shamir-Adleman (RSA), Diffie-Hellman, and ECDSA.
Both the Internet Engineering Task Force and the National Institute of Standards and Technology (NIST) recognize that classical elliptic curve systems would be vulnerable in the presence of a cryptographically relevant quantum computer (CRQC).
Buterin’s Ethereum research post on a potential quantum emergency highlights a key subtlety of Ethereum. If you have never spent from an address, only the hash of your public key will appear on-chain, and this is still believed to be completely secure. Once you send a transaction, your public key is exposed, giving a future quantum attacker the raw materials needed to recover your private key and drain the account.
So, the primary risk is not that quantum computers break Keccak or Ethereum data structures; Rather, it is that the future machine can target any address whose public key has been disclosed, which covers most user wallets and many smart contract vaults.
What Buterin said and how he portrays the risks
Buterin’s recent comments have two main pieces.
The first is to estimate the probability. Instead of second guessing himself, he pointed to Metaculus Expectations Which puts the chance of quantum computers being able to crack today’s public-key encryption at about one in five before 2030. The same forecast puts the average scenario around 2040. His argument is that even this kind of tail risk is high enough for Ethereum to prepare for in advance.
The second is framing 2028. Reportedly, in Devconnect He said The audience declared that “elliptic curves are going to die,” citing research suggesting that quantum attacks on 256-bit elliptic curves might become possible before the US presidential election in 2028. Some coverage compressed this into a headline like “Ethereum Has Four Years,” but its message was more nuanced:
-
Current quantum computers cannot attack Ethereum or Bitcoin today.
-
Once CRQCs are in place, ECDSA and related systems become structurally insecure.
-
Migrating a global network to post-quantum schemes takes years, so waiting for the obvious danger is itself risky.
In other words, he thinks like a safety engineer. You can’t evacuate a city because there’s a 20% chance of a major earthquake in the next decade, but you reinforce bridges while you still have time.
Did you know? The latest IBM products Road map It combines new quantum chips, Nighthawk and Loon, with the goal of demonstrating fault-tolerant quantum computing by 2029. It also recently showed that a key quantum error correction algorithm can run efficiently on conventional AMD hardware.
Inside the challenging ‘quantum emergency’ plan
Long before these recent public warnings, Buterin Developed a 2024 Ethereum research publication Titled “How to Hard Fork to Save Most Users Money in a Quantum Emergency.” It charts what Ethereum could do if a sudden quantum hack disrupts the ecosystem.
Imagine a public announcement about large-scale quantum computers going live and attackers draining already secure ECDSA wallets. So what?
Detect attack and retreat
Ethereum will restore the chain to the last block before large-scale quantum theft becomes clearly visible.
Disable legacy EOA transactions
Traditional externally owned accounts (EOAs) that use ECDSA will be frozen from sending funds, which will prevent further theft through exposed public keys.
Route everything through smart contract wallets
The new transaction type will allow users to prove, by Stark zero knowledgethey control the original path or derivation path – for example, a Bitcoin Improvement Proposal (BIP) 32 HD wallet pre-image, for a vulnerable address.
The manual will also specify a new verification code for quantum resistance Smart contract wallet. Once verified, control of the funds passes to that contract, which can enforce post-quantum signatures from that point on.
Boost proofs for gas efficiency
Given the large size of the STARK proofs, the design anticipates assembly. Aggregators send packets of proofs, allowing multiple users to move at once while keeping each user’s secret initial image private.
Most importantly, this is positioned as a last resort recovery tool, not a plan A. Buterin’s argument is that much of the plumbing protocol needed for such a fork, incl Account extractionstrong ZK resistance Quantitatively secure signature systems and schemes can and should be built.
In this sense, preparing for quantum emergencies becomes a requirement for designing the Ethereum infrastructure, not just an interesting thought experiment.
What experts say about timelines
If Buterin is relying on common expectations, what do hardware and cryptographers actually say?
On the hardware side, Google’s Willow chip, unveiled in late 2024, is one of the most advanced general quantum processors to date, with 105 physical qubits and error-correcting logical qubits that can beat classical supercomputers on specific benchmarks.
However, Google’s director of quantum artificial intelligence was clear that “the Willow chip is unable to break modern encryption.” he Estimates Breaking RSA would require millions of physical qubits and take at least 10 years.
Academic resources point in the same direction. One is widely cited analysis He found that breaking a 256-bit elliptic curve cipher within an hour using code-protected surface qubits would require tens to hundreds of millions of physical qubits, far exceeding anything available today.
On the cryptography side, the National Institute of Standards and Technology (NIST) and academic groups at places like MIT have done this to caution For years, once cryptographically relevant quantum computers exist, they will essentially break all widely deployed public key systems, including RSA, Diffie-Hellman, Elliptic Curve Diffie-Hellman, and ECDSA, through Shor’s algorithm. This applies both retrospectively, by decrypting collected traffic, and prospectively, by forging signatures.
That’s why NIST has spent nearly a decade running the Post-Quantum Cryptography Competition, and in 2024, It’s finished Its first three PQC standards: ML-KEM for key encapsulation and ML-DSA and SLH-DSA for signatures.
There is no consensus among experts on a specific “Q day.” Most estimates range from 10 to 20 years, although some recent work presents optimistic scenarios where fault-tolerant attacks on elliptic curves could be possible in the late 2020s under strong assumptions.
Policy bodies like the US White House and the National Institute of Standards and Technology take the risk seriously enough to push federal regulations toward PQC by the mid-2030s, which implies an unparalleled chance of crypto-related quantum computers arriving on that horizon.
In light of this, Buterin’s formulation of “20% by 2030” and “possibly before 2028” forms part of a broader range of risk assessments, where the real message is uncertainty as well as long time frames for migration, rather than the idea of a code-breaking machine on the internet being a secret today.
Did you know? National Institute of Standards and Technology and the White House 2024 report Estimates It will cost about $7.1 billion for US federal agencies to migrate their systems to post-quantum cryptography between 2025 and 2035, and that’s just one country’s government IT package.
What should change in Ethereum if quantum progress accelerates?
On the protocol and wallet side, several chains are already converging:
Account abstraction and smart contract wallets
Moving users from bare EOs to upgradeable smart contract wallets, through ERC-4337-style account stripping, makes it much easier to switch signing schemes later without emergency hard forks. Some projects are already offering Lamport-style quantum-resistant wallets or the Extended Merkle Signing System (XMSS) on Ethereum today.
Post-quantum signature schemes
Ethereum will need to choose (and battle-test) one or more PQC signature families (likely from NIST’s ML-DSA/SLH-DSA or hash-based constructions) and work through trade-offs in key size, signature size, verification cost, and smart contract integrity.
Cryptographic flexibility for the rest of the stack
Elliptic curves are not only used for user keys. BLS signatures, KZG obligations, and some proof-of-collection systems also rely on discrete record hardness. A serious, quantum-resilient roadmap needs alternatives to those core elements as well.
On the social and governance side, Buterin’s proposal for a quantum emergency fork is a reminder of how much coordination any real response requires. Even with perfect encryption, rolling back blocks, freezing old accounts, or forcing a mass migration of keys would be politically and operationally controversial. This is part of the reason he and other researchers say:
-
Build a kill switch or sleeve Canary Mechanisms that can automatically trigger migration rules once a smaller, vulnerable test asset is proven to be intentionally broken.
-
Treat post-quantum migration as an incremental selection process that users can adopt long before any credible attack rather than a last-minute scramble.
For individuals and organizations, the near-term checklist is simpler:
-
Prefer wallets and custodial setups that can upgrade their encryption without forcing a move to entirely new addresses.
-
Avoid unnecessary reuse of addresses so that fewer public keys are exposed on the chain.
-
Track Ethereum’s post-quantum signing options and be ready to migrate as soon as powerful tools become available.
Quantum risks should be treated in the same way that engineers think about floods or earthquakes. It’s unlikely your home will be destroyed this year, but it’s likely enough over a long period that it will make sense to design the foundation with that in mind.





